Deploying FRP Service on CentOS 7 to Achieve Intranet Penetration
Publish: 2019-03-14 | Modify: 2019-11-04
FRP is a high-performance reverse proxy application that can be used for intranet penetration. It supports TCP and UDP protocols and provides additional capabilities for HTTP and HTTPS application protocols. It also supports peer-to-peer penetration on a trial basis.

If you have used services like Peanut Shell, you may be familiar with the term FRP. FRP can achieve public network penetration into the intranet, even if your intranet machine does not support a public network IP. However, services like Peanut Shell usually limit traffic or require additional payment, and there are certain security risks. If you have your own VPS, you can easily set up FRP. This article shares an open-source project from GitHub, using CentOS 7 X64 as an example.
Prerequisites
FRP consists of a server-side and a client-side. The goal of this article is to penetrate into the intranet to connect to a Windows PC. Before we start, let's take a look at the FRP architecture diagram.
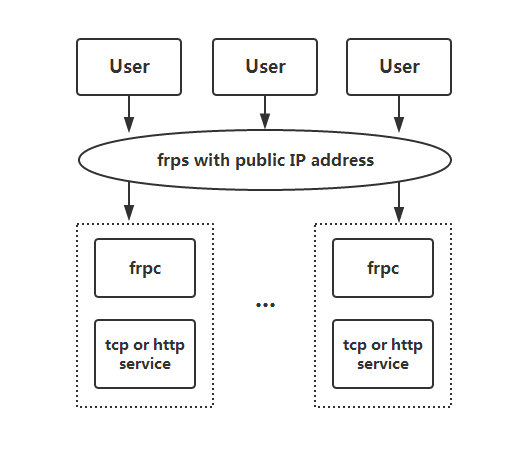
Install FRP Server
The author has provided pre-compiled binary packages. Download and extract them, then modify the configuration file.
# Download the server-side
wget https://github.com/fatedier/frp/releases/download/v0.25.0/frp_0.25.0_linux_amd64.tar.gz
# Extract
tar -zxvf frp_0.25.0_linux_amd64.tar.gz
# Enter the directory
cd frp_0.25.0_linux_amd64After extraction, you will see several files inside. We only need the following two files for the server-side.
-rwxrwxr-x 1 mysql mysql 11026848 Mar 11 17:15 frps
-rw-rw-r-- 1 mysql mysql 26 Mar 11 17:19 frps.iniContinue to edit the frps.ini file and write the following content:
[common]
bind_port = 7000
[mstsc]
listen_port = 3389
auth_token = 123456- bind_port: The port that the main server needs to listen on, using 7000 here.
- listen_port: The port to be forwarded, using 3389 here.
- auth_token: Equivalent to a verification password, using 123456 here, or you can leave it blank.
After completing the configuration file, enter the command ./frps -c ./frps.ini to start the server-side. Don't forget to open the port in the firewall. If you want the service to run in the background, you can replace the command with: nohup ./frps -c ./frps.ini &
# Open the port in iptables
iptables -A INPUT -p tcp --dport 7000 -j ACCEPT
iptables -A INPUT -p tcp --dport 3389 -j ACCEPT
service iptables save
# Open the port in firewalld
firewall-cmd --zone=public --add-port=7000/tcp --permanent
firewall-cmd --zone=public --add-port=3389/tcp --permanent
firewall-cmd --reloadInstall Windows Client
As mentioned earlier, FRP consists of a server-side and a client-side. The above steps have completed the server-side installation. Next, let's install the client-side on Windows.
- Windows client download link: frp_0.25.0_windows_amd64.zip
After extraction, we need the following two files for the client-side.
frpc.exe
frpc.iniModify the frpc.ini configuration file with the following content:
[common]
server_addr = 1.1.1.1
server_port = 7000
[mstsc]
type = tcp
local_ip = 127.0.0.1
local_port = 3389
remote_port = 3389
auth_token = 123456- server_addr: The public IP address of the server.
- server_port: The port that the FRP main server listens on.
- local_ip: The IP address of the local computer.
- local_port: The port that the local computer listens on (Windows Remote Desktop Service listens on 3389 by default).
- remote_port: The port that the server-side needs to forward.
- auth_token: The verification password, which we set as 123456 in the previous step.
In the cmd window, go to the FRP client directory and then execute the command frpc.exe -c frpc.ini. If there are no errors, the client-side is running normally. If your server IP is 1.1.1.1, when you connect to 1.1.1.1:3389, it will be mapped to 127.0.0.1:3389 in the intranet, thus achieving intranet penetration.
Summary
The above method is suitable for those who cannot obtain a public network IP locally. If you already have a public network IP locally, you can directly use the port mapping function of the modem or router. The above work only forwards TCP traffic, and the use of FRP goes far beyond this. If you are interested, you can explore it further.
- GitHub project address: https://github.com/fatedier/frp
- Latest server/client download: https://github.com/fatedier/frp/releases
- This article refers to: https://github.com/fatedier/frp/blob/master/README_zh.md
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- Multi-functional File Sharing Program Zdir 4.0.4 Update: Support for File Copy and Move (End of Article Bonus)
- Solving Access Challenges: Building Your Own Docker Image Proxy Acceleration Service with Nexus 3
- WildCard Virtual Card Guide: Quickly Set Up OpenAI/ChatGPT Payments
- Tencent Cloud "Cloud+ Campus Support Program": 360 yuan for a 3-year 1-core 2GB 1M server
- Raksmart USA VPS Limited Time 35% Off, Renewal at the Same Price
- Exclusive November Account Opening Promotion at Huashengtong: Get 600 HKD Cash Voucher + 400 HKD Stock
- Using Your Own SSL Certificate with mailcow (Part 2)
- Building a Poste Mail Server with Docker
- Setting up KeePass for Chinese and Chrome Auto-Fill Passwords
- Recommend a private photo album software suitable for NAS deployment: MT Photos