Installing fail2ban + Firewalld on CentOS 7 to prevent brute force and CC attacks
Publish: 2018-01-03 | Modify: 2019-05-29
fail2ban can monitor your system logs and take corresponding blocking actions based on the error messages in the logs. Most tutorials online are about fail2ban + iptables combination. Considering that CentOS 7 comes with Firewalld and using Firewalld as the network firewall is simpler and more convenient, I will share the method of using fail2ban + Firewalld.

Check if Firewalld is enabled
# If you have installed iptables, it is recommended to stop it first
service iptables stop
# Check the status of Firewalld
firewall-cmd --state
# Start Firewalld
systemctl start firewalld
# Set it to start automatically on boot
systemctl enable firewalld.serviceAfter enabling Firewalld, all ports are blocked by default, so be sure to allow access to commonly used ports to avoid being blocked. Here is an example of allowing SSH port (22):
# Allow port 22
firewall-cmd --zone=public --add-port=80/tcp --permanent
# Reload the configuration
firewall-cmd --reload
# Check the ports that have been allowed
firewall-cmd --zone=public --list-portsInstall fail2ban
fail2ban can monitor system logs and block IP addresses using Firewalld based on certain rules, which is especially effective for preventing brute-force attacks and scans.
# CentOS does not include fail2ban in its default repository, so you need to install EPEL repository first
yum -y install epel-release
# Install fail2ban
yum -y install fail2banAfter successful installation, the fail2ban configuration file is located at /etc/fail2ban. The jail.conf file is the main configuration file, and the related matching rules are located in the filter.d directory. Other directories/files are rarely used, but you can search for more information if needed.
Configure rules
Create a new jail.local file to override some of the default rules of fail2ban:
# Create a new configuration file
vi /etc/fail2ban/jail.local
# Default configuration
[DEFAULT]
ignoreip = 127.0.0.1/8
bantime = 86400
findtime = 600
maxretry = 5
# The banaction must be set to firewallcmd-ipset, which is supported by Firewalld. If you are using iptables, do not specify this.
banaction = firewallcmd-ipset
action = %(action_mwl)signoreip: IP whitelist, IP addresses in the whitelist will not be blocked. Multiple IP addresses can be separated by commas (,).bantime: Blocking time in seconds (s).findtime: Time range.maxretry: Maximum number of retries.banaction: Method used to block IP addresses. In the example above, Firewalld is used to block ports.action: Action to take.
Prevent SSH brute-force attacks
If you are still using the default SSH port (22), you may be scanned every day. It is highly recommended to strengthen the server protection according to the article "Linux Server Login Security" or you can use fail2ban to block malicious IP addresses.
Continue to modify the jail.local configuration file and add the following content:
[sshd]
enabled = true
filter = sshd
port = 22
action = %(action_mwl)s
logpath = /var/log/secure[sshd]: Name, can be filled in randomly.filter: Rule name, must be a rule located in thefilter.ddirectory,sshdis a built-in rule in fail2ban.port: Corresponding port.action: Action to take.logpath: Path to the log file to be monitored.
At this point, our jail.local rules may look like the following:
[DEFAULT]
ignoreip = 127.0.0.1/8
bantime = 86400
findtime = 600
maxretry = 5
banaction = firewallcmd-ipset
action = %(action_mwl)s
[sshd]
enabled = true
filter = sshd
port = 22
action = %(action_mwl)s
logpath = /var/log/secureThe above configuration means that if the same IP address exceeds 5 consecutive errors within 10 minutes, it will be blocked using Firewalld. Enter systemctl start fail2ban to start fail2ban and see the effect.
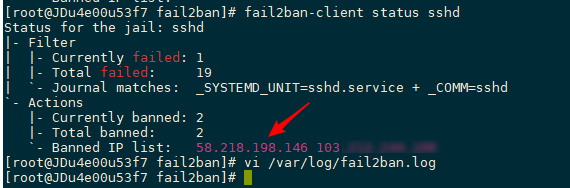
Try to connect to SSH from another server and enter the wrong password continuously. You will find that you cannot connect after exceeding 5 consecutive attempts, which means the IP address has been blocked. You can enter fail2ban-client status sshd to view the blocked IP addresses. See the screenshot below.
Prevent CC attacks
Here is an example using Nginx. Use fail2ban to monitor the Nginx logs, match the IP addresses that make frequent requests within a short period of time, and block them using Firewalld to prevent CC attacks.
# Create a new Nginx log matching rule
vi /etc/fail2ban/filter.d/nginx-cc.conf
# Add the following content
[Definition]
failregex = <HOST> -.*- .*HTTP/1.* .* .*
ignoreregex =Continue to modify vi /etc/fail2ban/jail.local and add the following content:
[nginx-cc]
enabled = true
port = http,https
filter = nginx-cc
action = %(action_mwl)s
maxretry = 20
findtime = 60
bantime = 3600
logpath = /usr/local/nginx/logs/access.logThe above configuration means that if the same IP address makes 20 requests within 60 seconds, it will be blocked for 1 hour. The configuration above is just for testing, please modify it according to your actual situation. logpath is the path to the Nginx logs.
Prevent WordPress brute-force attacks
If you often analyze logs, you will find that there are many bots scanning the WordPress login page wp-login.php. Although they may not succeed, it is better to block their IP addresses just in case.
# Create a new WordPress log matching rule
vi /etc/fail2ban/filter.d/wordpress.conf
# Add the following content
[Definition]
failregex = ^<HOST> -.* /wp-login.php.* HTTP/1\.."
ignoreregex =Continue to modify jail.local and add the following content:
[wordpress]
enabled = true
port = http,https
filter = wordpress
action = %(action_mwl)s
maxretry = 20
findtime = 60
bantime = 3600
logpath = /usr/local/nginx/logs/access.logDon't forget to enter systemctl restart fail2ban to restart fail2ban and make it effective.
Common commands
# Start fail2ban
systemctl start fail2ban
# Stop fail2ban
systemctl stop fail2ban
# Enable fail2ban to start on boot
systemctl enable fail2ban
# View blocked IP addresses (replace sshd with the rule name, e.g., [wordpress])
fail2ban-client status sshd
# Remove a blocked IP address
fail2ban-client set sshd delignoreip 192.168.111.111
# If the above command fails, try the following command
fail2ban-client set sshd unbanip 192.168.111.111
# View logs
tail /var/log/fail2ban.logConclusion
fail2ban has built-in many matching rules located in the filter.d directory, including commonly used SSH/FTP/Nginx/Apache log matching rules. If they still cannot meet your needs, you can create your own rules to match abnormal IP addresses. Using fail2ban + Firewalld to block malicious IP addresses is an effective way to improve server security.
This article is partially referenced from: CentOS 7安装Fail2ban防御暴力破解密码(配合FirewallD)
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- Solving the "Too many open files" issue with Nginx
- I Implemented Wireless Network Wake-up Using an Abandoned Wireless Router
- CloudCone's Latest Promotion: Starting from $2.8/month
- NanaZip: Clean and Ad-Free Modern Compression Software
- Using cron for scheduling tasks in Golang
- Let's talk about the virtual product delivery system "Delivery100" program.
- Chat about the enterprise email service provided by Zoho Mail Lite
- Disable PayPal Pre-authorized Payments to Avoid Automatic Deductions
- Installing supervisord on Centos 7.X
- Upgrade to the latest kernel and enable Google BBR on CentOS 6/7