Installing Firewalld Firewall and Common Commands in CentOS 7
Publish: 2018-09-03 | Modify: 2021-03-26
firewalld is a firewall management tool for Linux operating systems. It provides firewall functionality by acting as a front-end to the netfilter framework of the Linux kernel, similar to iptables.

Installing firewalld
By default, CentOS 7 may already have the firewalld service installed. If it is not installed, you can use the yum command to install it:
# Install firewalld
yum -y install firewalldPreparing to run firewalld
The default rules of firewalld already allow SSH service (port 22), but if you have modified the SSH port, you must allow it first. Otherwise, once firewalld is enabled, you will be blocked from accessing the server.
For example, if you have changed the SSH port to 2018, you can directly edit the firewalld configuration file vi /etc/firewalld/zones/public.xml and add the following rule:
<port protocol="tcp" port="2018"/>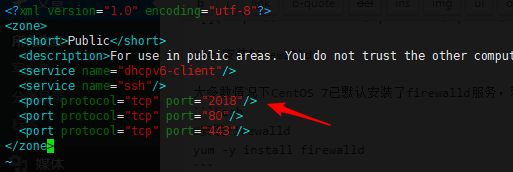
Alternatively, it is not recommended to directly modify the configuration file as it can easily lead to mistakes. Recently, I found out that the firewall-offline-cmd command can be used to execute commands offline:
firewall-offline-cmd --zone=public --add-port=2018/tcpThen enter the command: systemctl start firewalld to start firewalld and prevent being blocked.
Common commands
After installation, firewalld is not running. It is necessary to familiarize yourself with some basic commands:
# Check the running state
firewall-cmd --state
# Start firewall
systemctl start firewalld
# Enable on boot
systemctl enable firewalld
# Disable on boot
systemctl disable firewalld
# Stop firewall
systemctl stop firewalldIf you receive the error message "Failed to start firewalld.service: Unit firewalld.service is masked." when starting, you can resolve it by entering the following command:
systemctl unmask firewalld.serviceSome common examples
Allow a specific TCP port, such as port 80:
firewall-cmd --zone=public --add-port=80/tcp --permanentAllow a range of ports (8000-9000):
firewall-cmd --zone=public --add-port=8000-9000/tcp --permanentView the ports that have been allowed:
firewall-cmd --zone=public --list-portsRemove an allowed port (6022):
firewall-cmd --zone=public --remove-port=6022/tcp --permanentBlock a specific IP address (123.57.22.204) from connecting:
firewall-cmd --permanent --add-rich-rule="rule family=ipv4 source address=123.57.22.204 reject"Only allow specific IP addresses to access specific ports:
firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="101.32.40.130" port protocol="tcp" port="3306" accept"Note: All of the examples above require entering the command: firewall-cmd --reload to reload the firewall and make the changes take effect.
Conclusion
I personally find firewalld easier to use than iptables. The fact that CentOS 7 defaults to using firewalld as the firewall also has its reasons. So it would be a good idea to bookmark this article (imagine an evil smiley face here). The above examples provide the basic usage of firewalld, which should be sufficient for most situations. If you need to understand the meaning of the parameters in more detail, you can search online for more information.
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- Markdown-Temp: Your Online Temporary Document
- Windows Azure Exceeded Limits, Almost Crashed the Website
- OneNav 1.0.0 Official Release: New Batch Link Checking Feature
- OneNav Browser Extension 1.1.0 Refactored and Released
- Powerful Pan Download for High-speed Downloads on Baidu Netdisk
- Is Watching Movies on Pico Neo 3 VR All-in-One Headset Fun?
- Validating CloudFlare Certificate Requests with Nginx Location Matching
- Markdown Temp supports sending documents to WizNote.
- Quickly Create Cloud Servers with DigitalOcean
- Long wait, ImgURL Pro Image Hosting Source Code 2.0.0 officially released, bonus at the end of the article