One-click Installation of DNSmasq on CentOS
Publish: 2017-08-31 | Modify: 2019-04-29
DNSmasq is a small and convenient tool for configuring DNS and DHCP, suitable for small networks. It provides DNS functionality and optional DHCP functionality. In the article "Linux Installation of DNSmasq to Build Your Own Public DNS", the manual configuration method was shared, but due to the unfamiliarity of some friends with Linux, xiaoz wrote a one-click script.
Environment
- CentOS 6.x 7.x
Features of the Script
- One-click installation, zero configuration required
- Automatic release of TCP/UDP ports
- Access to the internet (Google and Facebook)
- Automatic update of hosts list
Installation
Copy the following commands for installation, one line at a time.
wget https://raw.githubusercontent.com/helloxz/dnsmasq/master/dns.sh --no-check-certificate
chmod +x dns.sh
./dns.shUsage
Refer to the article "Windows 7 DNS Settings Tutorial" to change the DNS to your server IP.
Common Problems
-
How to determine if DNSmasq is running normally? Enter the command
netstat -apn|grep 'dns'. If you see the screenshot below, it means that DNSmasq is running normally.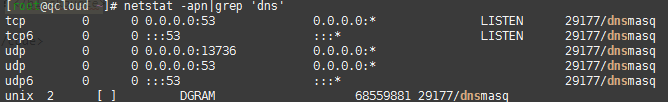
-
Configured DNS but unable to access the internet, showing DNS not found?
- Case 1: Check if the server supports security group function. Please check if TCP/UDP port 53 is open in the security group.
- Case 2: If you are using Tencent Cloud server, the script obtains the public IP. You need to modify the configuration file
/etc/dnsmasq.confand changelisten-address=to the private IP, as shown in the screenshot below.
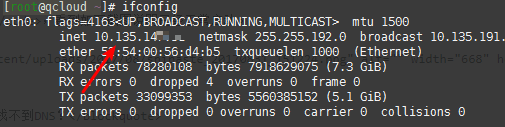
If you encounter any other problems, please leave a comment below.
Additional Information
It is recommended to use a domestic server for deployment, otherwise the resolution speed will be slow. If you want to implement features such as ad blocking, you need to modify the configuration rules yourself.
- Source Code: https://github.com/helloxz/dnsmasq
Additional Note
On September 19th, the blocking was upgraded. YouTube and Facebook have been added to the special care list and are treated the same as *.twitter.com. If the official IP (IPv4) is used and the corresponding domain's CA certificate is detected by the firewall, communication with the IP will be completely blocked. If an SNI server IP is used to proxy some domains, they will also be blocked, but not all IPs will be blocked, and very few IPs can be used. The blocking is only targeted at the exit route. In the near future, technologies such as CA certificate blocking will be fully deployed, and hosts files will become history!
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- Huawei Cloud Mid-Year Promotion: Cloud Servers Starting from 88 RMB/Year
- Installing MinDoc Documentation System on CentOS 7
- Get 30% off discount code for Hengchuang Hosting
- ImgURL Pro Professional Edition Image Hosting Program 2.1.0 Update, There are Benefits at the End of the Article
- Record of Flashing European Version MIUI 12.5 on Chinese Xiaomi 9 SE
- Using Wails: Easily Build Desktop Applications by Combining Go and Web Technologies
- Webmaster, come in! Get your free Alibaba Cloud coupon now!
- Sharing My Personal Experience with the Redmi Note 11T Pro as a Backup Phone
- bsdev.cn Services to be Shut Down & Latest Public Service Overview
- Unboxing and Experience of QNAP TS-453B mini