WordPress Exposes Stored XSS Vulnerability, Affects Versions 4.2 and Below
Publish: 2015-04-30 | Modify: 2015-04-30
Just a few days ago, when Aliyun Shield detected it, it was prompted that the website had an XSS vulnerability. At that time, I didn't pay much attention to it. Later, I saw another article on another blog confirming this issue, and checking the update record of WordPress also confirmed that there was indeed an XSS vulnerability. It is recommended that webmasters upgrade to the latest version. Here are the details.

WordPress officially released a new version 4.1.2 on April 21, which mentioned fixing a serious stored XSS vulnerability. Soon after, someone provided the details of the vulnerability. The security research team Klikki Oy discovered that this vulnerability can still be exploited in the new version (<=4.2) of WordPress.
XSS Vulnerability One
This XSS vulnerability appeared in the comment section of WordPress, but the problem was caused by a feature of MySQL. In the utf8 character set of MySQL, a character is composed of 1 to 3 bytes. For characters larger than 3 bytes, MySQL uses utf8mb4 to store them. If we insert a utf8mb4 character into a column encoded in utf8, then in MySQL's non-strict mode, it will truncate the content after it.
Vulnerability details: By utilizing this feature, the author discovered this XSS vulnerability in WordPress. WordPress defaults to utf8 encoding and does not enable strict mode. If we add a comment like this:
<abbr title='WeIt will cause the layout of the WordPress page to be messed up. If we insert another comment like this, it will cause an XSS vulnerability.
cedric' onmouseover='alert(1)'
style='position:fixed;top:0;left:0;width:100%;height:100%'The page will be displayed like this:
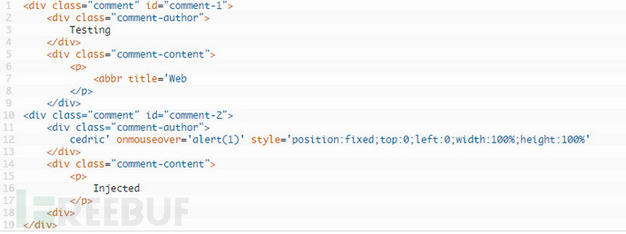
The author provided a proof of concept (POC):
sometext
<blockquote cite='x onmouseover=alert(1)
Affected versions: WordPress 4.1.1 and earlier versions are affected. It is said that version 4.1.2 has fixed this vulnerability.
XSS Vulnerability Two
Just recently, the security research team Klikki Oy discovered that this vulnerability can still be exploited in the new version of WordPress. The principle of how the vulnerability is formed is the same, using truncation to cause layout mess-up on the page. The only difference is that this time Klikki Oy used another feature of MySQL.
The column in the wp_comments table of WordPress that stores comments is comment_content, and its type is text. Text can store up to 64kb of data. If a user enters more than 64kb of data, MySQL will still truncate the content after it. Since WordPress does not limit the length of comment content, when we submit comment content larger than 64kb, it can still cause layout mess-up on the page and form an XSS vulnerability.
Below is the POC given by the Klikki Oy team:
<a title='x onmouseover=alert(unescape(/hello%20world/.source))
style=position:absolute;left:0;top:0;width:5000px;height:5000px
AAAAAAAAAAAA [64 kb] ...'></a>Affected versions: WordPress 4.2 and earlier versions are affected.
PS: In fact, Xiao Z doesn't know much about security. This vulnerability mainly targets comments. It is recommended that webmasters upgrade WordPress to the latest version or refer to the article "How to Effectively Block WordPress Spam Comments" to effectively block non-Chinese comments.
Original source: WordPress曝存储型XSS漏洞,影响4.2及以下版本
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- How is the website speed of DigitalOcean cloud hosting?
- Building Your Own Private Notes with Obsidian + Seafile: A Beginner's Guide
- A versatile download tool Motrix, supporting BT, magnet links, Baidu Cloud, and other resources
- AsBot Intelligent Assistant - Let Artificial Intelligence Help You Solve Problems
- Installing Transmission with Docker and using the enhanced UI
- 2 Tools for Detecting Backdoors in Website Program Source Code/Themes and More
- Solving the "Too many open files" issue with Nginx
- ImgURL, an open-source image hosting platform, updated to v2.1 with lowered system requirements
- The correct way to downgrade Vultr's original $5 package to $2.5
- [Essential for Development] ApiPost: A Cross-Platform API Management and Debugging Tool