Installing SNI Proxy on CentOS 7 for Reverse Proxying HTTPS Sites
Publish: 2020-07-22 | Modify: 2022-02-26
Introduction
One of the most common tools for reverse proxy is Nginx. If you want to use Nginx as a reverse proxy for an HTTPS site and access it through HTTPS, you need to configure SSL certificates on Nginx. However, SNI Proxy can solve this problem. With SNI Proxy, you don't need to deploy SSL certificates on the reverse proxy server to access HTTPS sites.
Example
Let's say one day you want to access https://www.google.com, but you find that you can't open it due to certain reasons. You start thinking if there is a way to access https://www.google.com without changing the domain name. This is where SNI Proxy comes in.
To help you understand better, I have created a simple diagram:
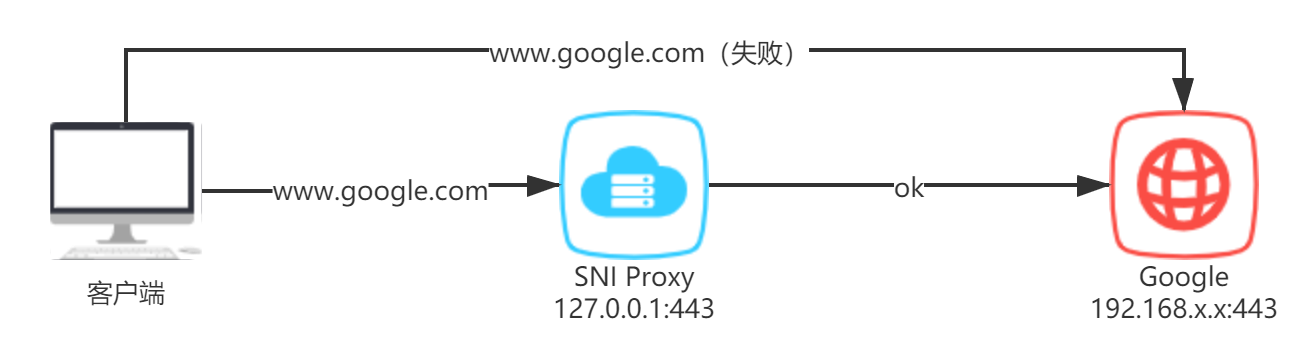
Installing SNI Proxy
First, install the required dependencies:
yum -y install gcc gcc-c++ autoconf automake curl gettext-devel libev-devel pcre-devel perl pkgconfig rpm-build udns-develNext, download and unzip the source code from https://github.com/dlundquist/sniproxy/releases. Navigate to the SNI Proxy directory and run the following commands to compile:
./autogen.sh && ./configure && make distIf the installation process completes without any errors, you can check the version by running the command sniproxy -V.

Creating the Configuration File and Starting SNI Proxy
The default configuration file for SNI Proxy is located at /etc/sniproxy.conf. You can refer to the following example for its contents:
user daemon
pidfile /tmp/sniproxy.pid
error_log {
syslog daemon
priority notice
}
listener 127.0.0.1:443 {
protocol tls
table TableName
# Specify a server to use if the initial client request doesn't contain
# a hostname
fallback 192.0.2.5:443
}
table TableName {
# Match exact request hostnames
example.com 192.0.2.10:4343
# If port is not specified, the listener port will be used
example.net [2001:DB8::1:10]
# Use regular expressions to match
.*\\.com [2001:DB8::1:11]:443
# Combine regular expression and wildcard to resolve the requested hostname
.*\\.edu *:443
}Finally, start SNI Proxy by running the command sniproxy. You can use ps -ef|grep 'sniproxy' to check if the process is running. Note: You also need to allow the listening port in the firewall.
Testing Access
You can modify the hosts file to point the domain name to the SNI Proxy server for testing if you can access it.
Conclusion
SNI Proxy has the advantage of simpler configuration compared to Nginx reverse proxy. You don't need to deploy SSL certificates on the SNI Proxy server, and the traffic is forwarded to the destination server based on the HOST field in the HTTP header. However, the suitability of SNI Proxy for high concurrency scenarios and its performance under heavy loads may vary. Additionally, combining SNI Proxy with a self-built DNS can be very effective.
SNI Proxy project: https://github.com/dlundquist/sniproxy
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- Simple Method for Setting Up V-*-* Server on DigitalOcean
- Another Open Source and Free SSH/SFTP Client: Electerm
- Cookies are blocked or your browser is not supported
- Google Cloud Free Trial: Get $300 for New User Registration
- Exploring the Starry Sky Network: NAS Users without Public IP Can Also Enjoy Smooth Network Connections
- Quickly Generate Website Thumbnails for PC, Tablets, and Mobile Devices
- YoMail Email Client, Might Be More to Your Taste
- SpeedDisk - Free from the Troubles of Baidu Cloud Disk Speed Limit
- Namecheap Domain Utilizes CloudXNS Intelligent Resolution
- Recording the Experience and Solutions of Failed aaPanel Installation Environment