Nginx using HTTP/2 and HTTPS benchmark testing
Publish: 2016-07-28 | Modify: 2017-06-21
HTTP 2.0, also known as Hypertext Transfer Protocol 2.0, is the next generation of HTTP protocol. It is being developed by the Internet Engineering Task Force (IETF). For detailed information, please refer to the Wikipedia page on HTTP 2.0.

If you haven't enabled HTTPS yet, please refer to the article on Nginx force HTTPS, HTTP 301 redirect to HTTPS. Enabling HTTP/2 support in Nginx is very simple, you just need to change listen 443; to listen 443 ssl http2;, and don't forget to reload Nginx.
HTTP/2 Testing
After enabling HTTP/2, how can you tell if your website supports it? You can install the "HTTP/2 and SPDY indicator" extension in Chrome/Firefox browsers. If a website supports HTTP/2, it will be displayed in blue. If it is gray, it means it does not support HTTP/2. Additionally, starting from Chrome 51, ALPN support is required, otherwise it will degrade to HTTP/1.1.
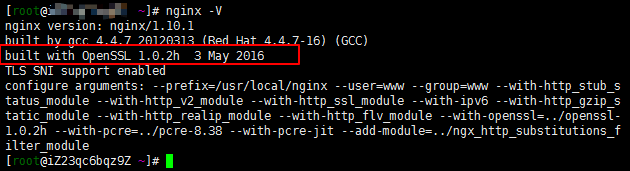
OpenSSL Version
ALPN requires OpenSSL 1.0.2 support. The latest version of OneinStack already supports OpenSSL 1.0.2. You can use the command nginx -V to check.
Nginx HTTPS Optimization
On V2, I saw a configuration rule shared by a netizen which significantly improved the score. You can directly use the following rules:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Allowed protocols
ssl_ciphers EECDH+CHACHA20:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5; # Encryption algorithms (recommended suite by CloudFlare)
ssl_prefer_server_ciphers on; # Optimize SSL cipher suite
ssl_session_timeout 10m; # Client session cache time
ssl_session_cache builtin:1000 shared:SSL:10m; # SSL session cache type and size
ssl_buffer_size 1400; # 1400 bytes to fit in one MTU
add_header Strict-Transport-Security max-age=15768000;
ssl_stapling on;
ssl_stapling_verify on;Below is the complete rule for XiaoZ's blog, you can refer to it if needed:
server {
listen 443 ssl http2;
ssl_certificate /data/ssl/xiaoz.me.crt;
ssl_certificate_key /data/ssl/xiaoz.me.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Allowed protocols
ssl_ciphers EECDH+CHACHA20:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5; # Encryption algorithms (recommended suite by CloudFlare)
ssl_prefer_server_ciphers on; # Optimize SSL cipher suite
ssl_session_timeout 10m; # Client session cache time
ssl_session_cache builtin:1000 shared:SSL:10m; # SSL session cache type and size
ssl_buffer_size 1400; # 1400 bytes to fit in one MTU
add_header Strict-Transport-Security max-age=15768000;
ssl_stapling on;
ssl_stapling_verify on;
server_name xiaoz.me www.xiaoz.me;
index index.html index.htm index.php;
include /usr/local/nginx/conf/rewrite/wordpress.conf;
root /data/wwwroot/xiaoz.me;
location ~ [^/]\.php(/|$) {
#fastcgi_pass remote_php_ip:9000;
fastcgi_pass unix:/dev/shm/php-cgi.sock;
fastcgi_index index.php;
include fastcgi.conf;
}
location ~ .*\.(gif|jpg|jpeg|png|bmp|swf|flv|ico)$ {
expires 30d;
access_log off;
}
location ~ .*\.(js|css)?$ {
expires 7d;
access_log off;
}
}
server {
listen 80;
server_name xiaoz.me www.xiaoz.me;
rewrite ^(.*) https://blog.xiaoz.org$1 permanent;
}HTTPS Score Testing
We can open SSL Labs to test our website's HTTPS score. If you have upgraded to OpenSSL 1.0.2 and enabled HTTP/2, you will see a significant improvement in the score. Below is a screenshot comparison from XiaoZ's blog:
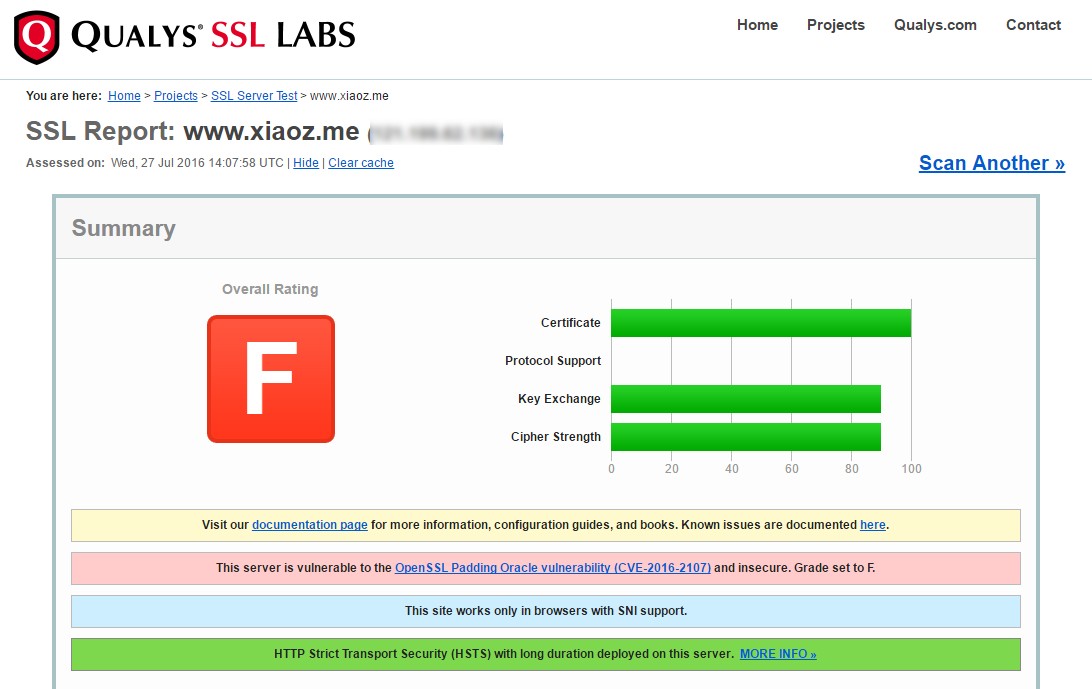 Before optimization (click to enlarge)
Before optimization (click to enlarge)
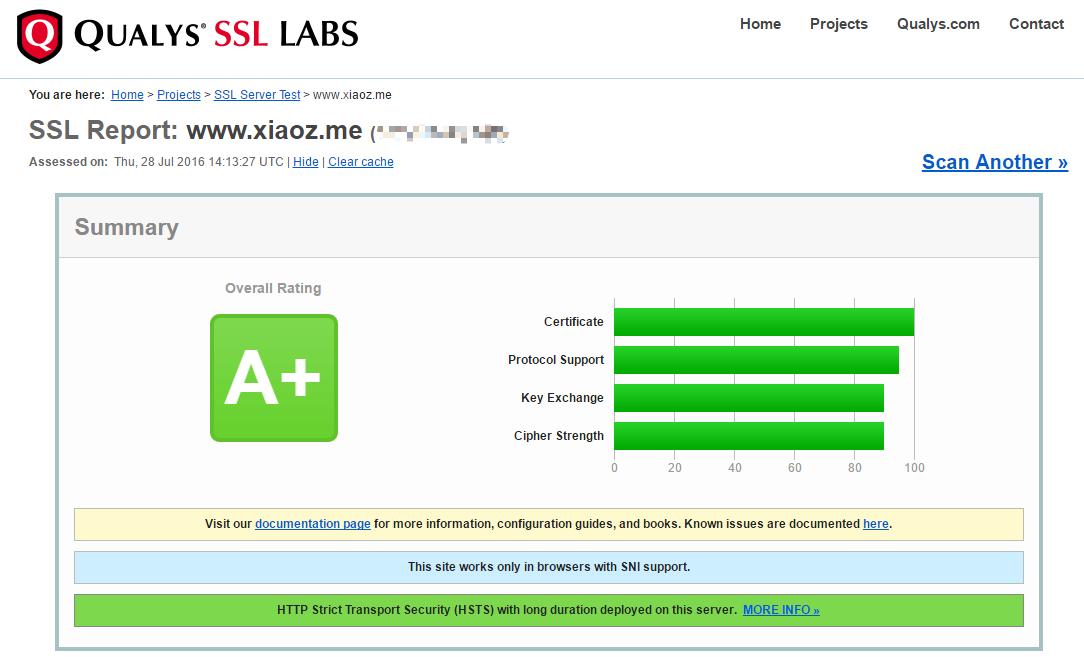 After upgrading OpenSSL 1.0.2 and optimization (click to enlarge)
After upgrading OpenSSL 1.0.2 and optimization (click to enlarge)
Conclusion
If you like to tinker, consider upgrading OpenSSL to 1.0.2. Please backup important configurations. Additionally, UCloud's CDN already supports HTTP/2. If you don't want to tinker, you can directly use UCloud's CDN, but you need a BA.
This article is referenced from: 为什么我们应该尽快支持 ALPN? 关于 Nginx 开启 HTTP/2 的问题
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- WiseTDIFw64.sys Causes Windows 10 to Continuously Blue Screen and Restart
- Parallels: A RDP Client Tool Supporting Socket5 and HTTP Proxies
- Raksmart Japan VPS (Mainland Optimized Network) Simple Evaluation
- PHP curl encounters SSL certificate problem: self signed certificate in certificate chain
- WordPress Blog Theme Msimple Updated to v1.1 with Update Instructions
- [AD] Comodo Positive SSL Certificate for only 98 yuan for two years
- Simplified judgment of whether it is a mobile visit - PointNet
- Implementing Automatic Keywords and Descriptions in WordPress Code
- Implementing a Beautiful Index Directory Using Fdscript
- [SEO Techniques] What technical skills should SEOers possess?