An Analysis of the Principles and Theoretical Foundations of HTTPS
Publish: 2019-11-17 | Modify: 2019-11-17
With the rapid development of the Internet, network security has been increasingly valued. The traditional HTTP protocol transmits data in plain text, which poses a great security risk if the HTTP request is intercepted by hackers and the content is easily obtained. In order to solve this problem, Netscape developed the HTTPS protocol, which encrypts data transmission. Even if a hacker intercepts the data during transmission, it cannot be deciphered, ensuring the security of network communication.
Cryptography Basics
Before understanding the HTTPS protocol, we first need to know some basics of cryptography.
- Plain Text: Plain text refers to the original data that has not been encrypted.
- Cipher Text: When plain text is encrypted using a certain encryption algorithm, it becomes cipher text, ensuring the security of the original data. Cipher text can also be decrypted to obtain the original plain text.
- Key: A key is a parameter used in the algorithm for converting plain text to cipher text or vice versa. Keys can be symmetric or asymmetric, used in symmetric encryption and asymmetric encryption respectively.
Symmetric Encryption
Symmetric encryption, also known as private key encryption, is when the sender and receiver of information use the same key to encrypt and decrypt data. Symmetric encryption is characterized by its publicly available algorithm, fast encryption and decryption speed, and suitability for encrypting large amounts of data. Common symmetric encryption algorithms include DES, 3DES, TDEA, Blowfish, RC5, and IDEA.
- Encryption process: Plain text + Encryption algorithm + Private key => Cipher text
- Decryption process: Cipher text + Decryption algorithm + Private key => Plain text
To put it simply, imagine there is a box with two identical keys, key A and key B. Key A puts a treasure map into the box and sends it to B through a courier. Without the key, no one knows what's inside the box. When B receives the box, they can use their key to open it and find the treasure map. This is symmetric encryption.
Asymmetric Encryption
Asymmetric encryption, also known as public key encryption, provides better security compared to symmetric encryption. In symmetric encryption, both communication parties use the same key. If one party's key is compromised, the entire communication can be decrypted. Asymmetric encryption uses a pair of keys, namely the public key and private key, which always appear together. The private key is kept by the owner and must not be disclosed. The public key is publicly available to anyone. Encryption can be done with either the public key or the private key, and decryption can be done with the other key.
Encryption with the public key can only be decrypted with the private key: Plain text + Encryption algorithm + Public key => Cipher text, Cipher text + Decryption algorithm + Private key => Plain text
Encryption with the private key can only be decrypted with the public key: Plain text + Encryption algorithm + Private key => Cipher text, Cipher text + Decryption algorithm + Public key => Plain text
As encryption and decryption use two different keys, this is why it's called asymmetric encryption. The main algorithms used in asymmetric encryption are RSA, Elgamal, Rabin, D-H, and ECC (Elliptic Curve Cryptography).
HTTPS Communication Process
HTTPS protocol = HTTP protocol + SSL/TLS protocol. During HTTPS data transmission, SSL/TLS is used to encrypt and decrypt data, while HTTP is used to transmit the encrypted data. Therefore, HTTPS is a combination of HTTP and SSL/TLS.
To ensure both security and efficiency, HTTPS uses both symmetric and asymmetric encryption. Before transmitting content, it uses asymmetric encryption to exchange public keys and client keys (this data is very small). When it comes to transmitting the actual content, it uses the client key for symmetric encryption (considering transmission efficiency).
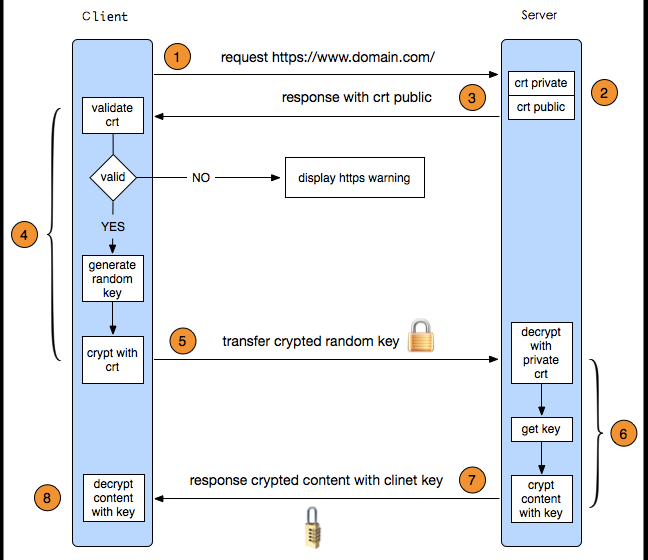
An HTTPS request actually consists of two HTTP transmissions, which can be divided into 8 steps:
- The client initiates an HTTPS request to the server, connecting to port 443 on the server.
- The server has a key pair, consisting of a public key and a private key, used for asymmetric encryption. The server keeps the private key and must not disclose it, while the public key can be sent to anyone.
- The server sends its public key to the client.
- After receiving the server's public key, the client checks and verifies its legitimacy. If any issues are found with the public key, the HTTPS transmission cannot continue. Strictly speaking, this step should verify the legitimacy of the server's digital certificate. How the client verifies the legitimacy of the digital certificate will be explained later. If the public key is valid, the client generates a random value, which is used as the key for symmetric encryption. This key is referred to as the client key, to distinguish it from the server's key. Then, the client encrypts the client key using the server's public key, turning it into cipher text. At this point, the first HTTP request in HTTPS is completed.
- The client initiates the second HTTP request in HTTPS, sending the encrypted client key to the server.
- After receiving the cipher text sent by the client, the server decrypts it using its private key, obtaining the client key. Then, the server uses the client key to symmetrically encrypt the data, turning it into cipher text.
- The server sends the encrypted cipher text to the client.
- The client receives the cipher text sent by the server and uses the client key to symmetrically decrypt it, obtaining the data sent by the server. This completes the second HTTP request in HTTPS, and the entire HTTPS transmission is finished.
The entire process is illustrated in the following diagram:
Summary
- HTTPS = HTTP + TLS/SSL, which encrypts the HTTP transmission process to ensure data security.
- HTTPS uses both asymmetric and symmetric encryption.
- Asymmetric encryption: Client initiates HTTPS request -> Server sends public key to client -> Client generates a random value and encrypts it with the public key -> Server decrypts the encrypted content with its private key to obtain the client's random value.
- Symmetric encryption: Server uses the random value to encrypt the transmitted content -> Client decrypts the encrypted content using the generated random value.
Some parts of this article are referenced from:
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- [Important] [Urgent] Temporary Backup Domain: https://blog.xiaoz.org
- Methods for connecting to V-P-N on Windows 7
- Building Your Own Wiki Knowledge Base with Wikitten
- ImgURL Pro Professional Edition Released, Support for Multiple External Storage, 20% Off Promotions
- Zdir 4.0.2 Update: Added File Creation and Text Editing Functions
- Sharing the Process of Migrating a Million-Data Website (imgurl.org)
- TangStyle optimized version uses CNZZ cloud recommendation
- Solution for Unable to Shut Down Virtual Machine in PVE
- Notice of Server Upgrade for Little Z's Blog
- Jiacrontab 2.x Release: A Simple and Reliable Task Management Tool with Support for Second-level Scheduled Tasks