Using acme.sh script to apply for Let's Encrypt wildcard SSL certificate
Publish: 2018-03-19 | Modify: 2018-06-17
Let's Encrypt is a certificate authority that was launched in 2015. It has been providing free SSL certificate services and today we have the long-awaited Let's Encrypt wildcard SSL certificate. It is very convenient to apply for it using acme.sh.
acme.sh implements the acme protocol and is an open-source tool for Let's Encrypt SSL application. It simplifies the operation and process compared to the official application method, so I recommend everyone to use it.
Install acme.sh
The following commands should be executed on a Linux system, and can be installed by both root and regular users.
# Install
curl https://get.acme.sh | sh
# Activate the alias
source ~/.bashrcSet up DNS API
Currently, wildcard certificates only support DNS validation. acme.sh automatically completes the operation through the API of the DNS provider. Therefore, you need to set up the DNS API first. Take CloudXNS as an example.
In the CloudXNS backend - User Center - API Management, you can see the API KEY/SECRET KEY. If you don't have it, please create it and record it.
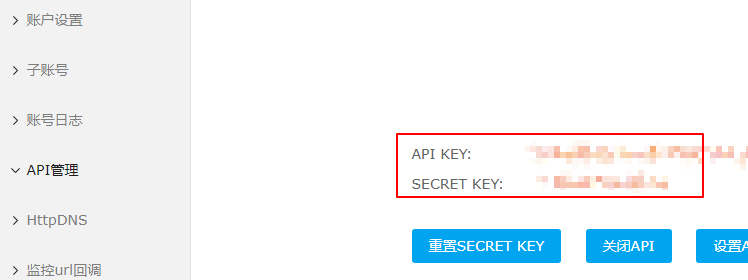
Enter the following command to import the key (CloudXNS). Note that different DNS providers have different import parameters. You can refer to dnsapi for specific information.
export CX_Key="1234"
export CX_Secret="sADDsdasdgdsf"- CX_Key: Corresponding to CloudXNS API KEY
- CX_Secret: Corresponding to CloudXNS SECRET KEY
Other commonly used DNS API settings
CloudFlare
# Import the key
export CF_Key="sdfsdfsdfljlbjkljlkjsdfoiwje"
export CF_Email="xxxx@sss.com"
# Apply for the certificate
acme.sh --issue --dns dns_cf -d example.com -d www.example.comTencent/DNSPod (Chinese version)
# Import the key
export DP_Id="1234"
export DP_Key="sADDsdasdgdsf"
# Apply for the certificate
acme.sh --issue --dns dns_dp -d example.com -d www.example.comAlibaba Cloud
# Import the key
export Ali_Key="sdfsdfsdfljlbjkljlkjsdfoiwje"
export Ali_Secret="jlsdflanljkljlfdsaklkjflsa"
# Apply for the certificate
acme.sh --issue --dns dns_ali -d example.com -d www.example.comFor more DNS API settings, please refer to here.
Issue a wildcard certificate
Taking CloudXNS DNS as an example, let's issue a wildcard certificate for awk.sh.
acme.sh --issue --dns dns_cx -d awk.sh -d *.awk.shAfter successful application, the absolute path of the certificate will be displayed (as shown in the screenshot below). You can deploy the SSL certificate on the web server.
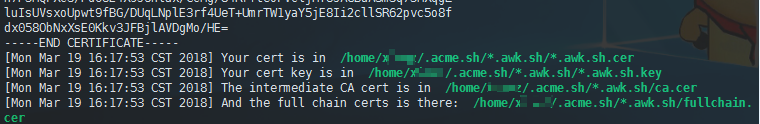
If you are using Nginx, you can refer to the article "How to Deploy SSL Certificates with Nginx" to deploy the SSL certificate. Generally, you only need the fullchain.cer and domain.com.key files.
Copy the certificate
After generating the certificate, you need to copy the certificate to the actual location where it is needed. The generated certificates are all placed in the installation directory: ~/.acme.sh/. Please do not use the files directly in this directory. The correct method is to use the --installcert command and specify the target location, then the certificate files will be copied to the corresponding location. For example:
acme.sh --installcert -d xiaoz.top \
--key-file /data/ssl/xiaoz.top.key \
--fullchain-file /data/ssl/xiaoz.top.cer \
--reloadcmd "service nginx force-reload"Summary
Currently, Let's Encrypt supports multiple domains and wildcard domains. However, the drawback is that the validity period is still only three months. Although you can set up a script for automatic renewal, it is still a bit inconvenient for management and maintenance.
Some content is referenced from: https://github.com/Neilpang/acme.sh
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- ChangeIP VPS, 25% off discount, Shark Room with direct connection to three networks, equipped with DDoS high defense
- DzzOffice: Open Source Free Office Suite (Enterprise Cloud Storage)
- Installation and Common Commands for Accelerating Your VPS with Rui Suo (Outdated)
- EchoTheme - A Minimalist Style Theme for Typecho
- [SEO Principles] What is the principle of optimizing SEO keyword rankings?
- Solution for Terminal Garbled Characters "^[[A^[[D" in Linux (Debian 11)
- Methods to Enable Cloud Clipboard on Windows 10
- Feelings from Operating ImgURL Free Image Hosting for 2 Years
- Installing Gogs on CentOS 7 to Build Your Own Git Repository
- [Tutorial] Let's Talk About Those Little DNS Knowledge