Preventing DDOS Attacks Initiated by WordPress Pingbacks
Publish: 2016-06-04 | Modify: 2017-06-21
Just two days ago, the blog server was hit by a DDOS attack. At first, the attacker used SYN attack on port 443, causing Nginx to exhaust its resources and the bandwidth to max out. Redirecting the traffic overseas did not help, so we had to shut down and go to sleep. After wave after wave of attacks, the attacker gave up SYN attack and started using WordPress pingback to launch the DDOS attack, rendering the website inaccessible.
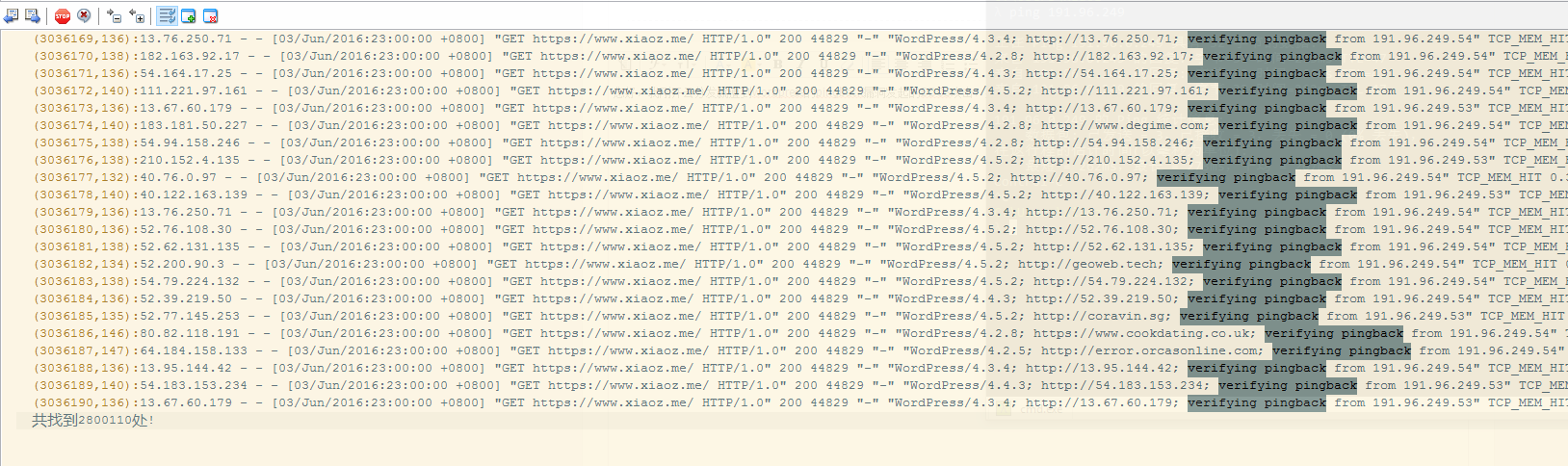
Disable pingback function
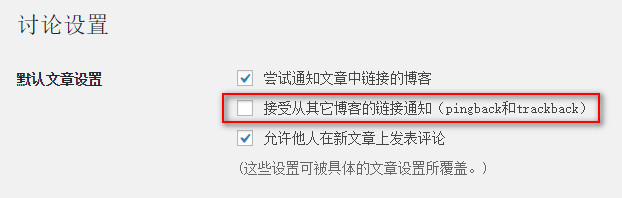
Pingback, translated as "引用 (quotation)" in Simplified Chinese, is actually a notification to inform the other party that something related to them has happened in that place. It is rarely used in general situations, so it is better to just disable it. Go to Settings -> Discussion -> Allow link notifications from other blogs (pingbacks and trackbacks) and uncheck the box, then save.
Modify Nginx configuration
If you are using Nginx as your web server, you can add the following code to the host configuration file, usually located at /usr/local/nginx/conf/vhost/yourdomain.conf, and add it inside the server block, then reload Nginx with service nginx reload.
if ($http_user_agent ~* "WordPress") {
return 403;
}CURL test
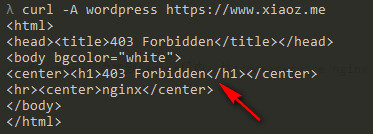
We can use CURL to simulate a request and see if it takes effect. If it returns a 403 error, it means the configuration is successful.
Additional information
After Nginx prohibits user_agent from WordPress, although it returns a 403 error, it still generates a large number of requests, which consumes server resources. You can add the following code to the functions.php file in the theme directory.
add_filter( 'xmlrpc_methods', function( $methods ) {
unset( $methods['pingback.ping'] );
return $methods;
} );Other notes
If your website is using a CDN service provided by a third party, you need to block WordPress pingback attacks by adding WordPress U-AGENT requests to the blacklist. For more detailed information, please refer to an article on the WooYun vulnerability website: http://drops.wooyun.org/news/1062
Comments

xiaoz
I come from China and I am a freelancer. I specialize in Linux operations, PHP, Golang, and front-end development. I have developed open-source projects such as Zdir, ImgURL, CCAA, and OneNav.
Random article
- NetCup European VPS Basic Review and Usage Precautions
- How to Check Which Process is Occupying Disk IO in Linux
- Easily Manage Your Docker Compose Projects with Dockage
- Open Source Image Hosting ImgURL v2.3 Released
- Linode launches $5 package, new users get $20 upon registration
- Using Qiniu Cloud Storage to Accelerate Gravatar Avatars
- Using Qiniu Cloud Storage to Host Images in Typecho without Plugins
- Scaleway offers free 75GB object storage service
- Exploring ProxyPin: Open Source Free Cross-Platform HTTP Capture Tool
- Improving Zoho Mail's Sending and Receiving Speed with Nginx Port Forwarding